
~Photo of
Heavy Stones Fear No Weathertaken by me in Reykjavik
If you’re like many people out there today you probably proxy traffic through CloudFlare’s WAF (Web Application Firewall).
You might also be aware that supporting TLSv1.0 and TLSv1.1 nowadays is considered “weak” when it comes to your security posture.
But why is using 1.0 and 1.1 a bad thing?
-
They don’t support newer cipher suites, and only allow the use of older ciphers that are no longer considered cryptographically secure.
-
They also use weak Hashing algorithms (SHA-1/MD5) for handshake authentication.
So what do we do?
We modify our nginx.conf to specify TLSv1.2 and TLSv1.3, test it with nginx -t and restart, done.
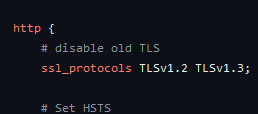
Easy; Now we can verify it worked with Qualys’ scanner and call it a day.
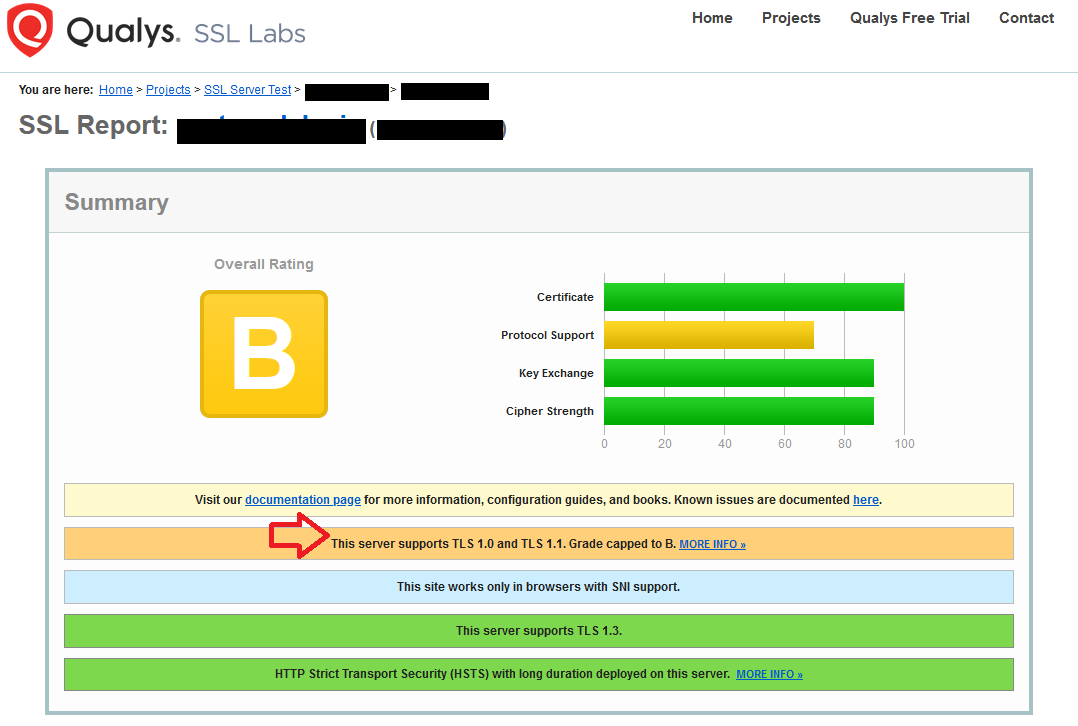
Whoops. Well what’s happening here is we disabled TLSv1.0 and 1.1 between CloudFlare and our server, but the Client is still using 1.0 and 1.1 when talking to CloudFlare.
Here’s an ascii diagram of what’s going on:
[CLIENT] --|1.0, 1.1, 1.2, 1.3|--> [CLOUDFLARE] --|1.2, 1.3|--> [NGINX]
^ ^
| This is what we changed
|
But this is where we actually
need to disable 1.0 and 1.1 to be secure
So lets configure CloudFlare to match our Nginx conf.
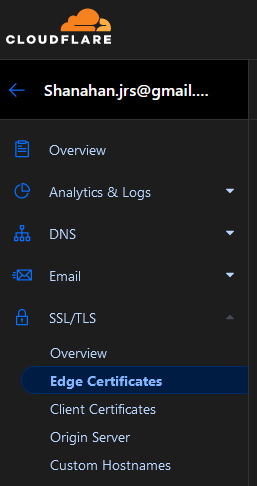
https://cloudflare.com/ > click your domain > SSL/TLS > Edge Certificates
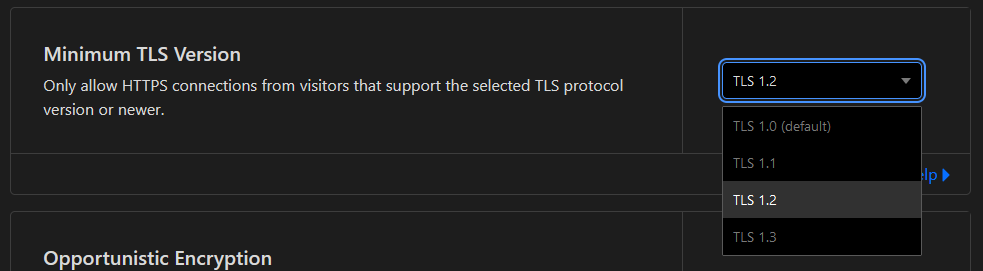
Once here scroll down until you find Minimum TLS Version and set it to TLS 1.2, it should auto save once clicked.
Now our connections look like this:
[CLIENT] --|1.2, 1.3|--> [CLOUDFLARE] --|1.2, 1.3|--> [NGINX]
And a quick rescan with Qualys show’s we’re right!
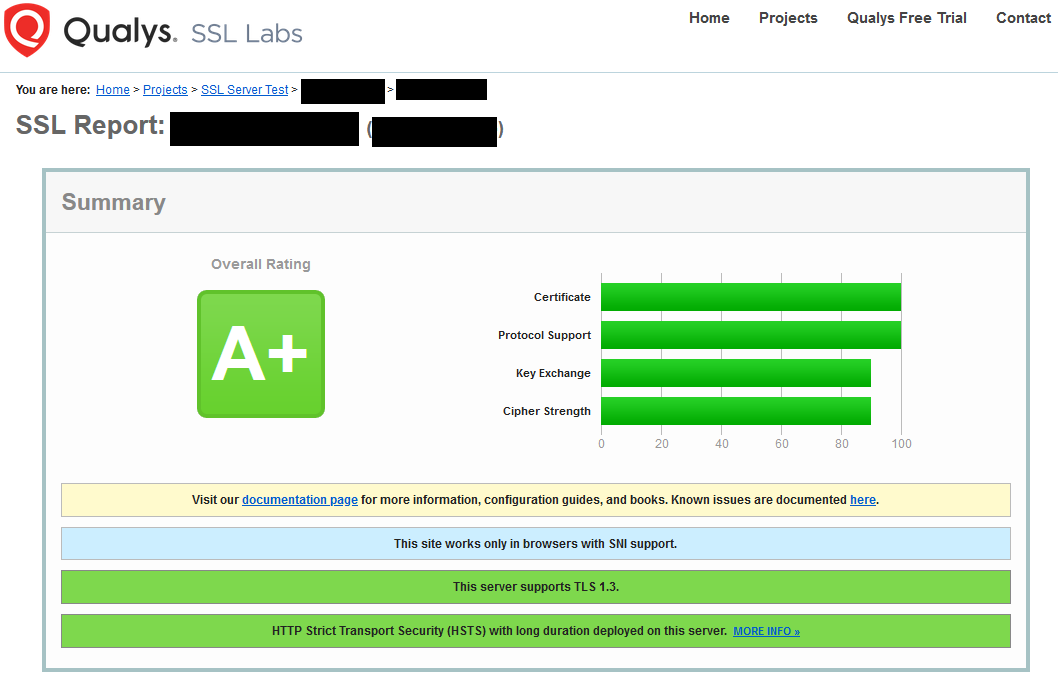
A lot of this is probably common knowledge for some people but it definitely took some digging for me to figure this out, so hopefully this helps someone!